Kong is one of the core technologies used by Mashape to power API request from developers.
Why do I need an API gateway?
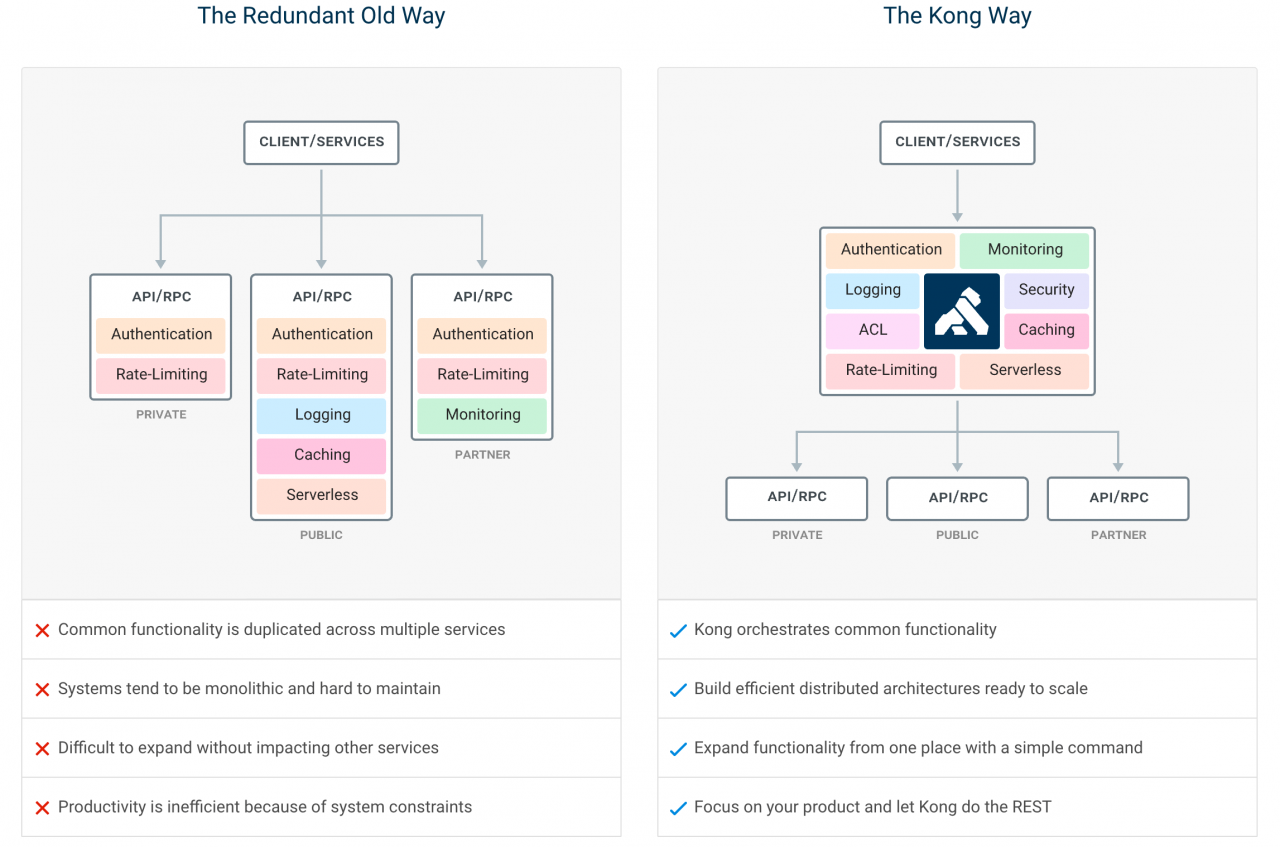
Under the micro-service architecture, services are dismantled in a very fragmented manner, which reduces the coupling and makes the unified management of services more difficult. As shown on the left of the figure above, under the old service governance system, authentication, current limiting, logging, monitoring and other general functions need to be implemented separately in each service, which makes the system maintainer do not have a global view to manage these functions. API gateway is dedicated to solve the problem of microservice nanotubes, which are common functions, and on this basis, improve the scalability of the system. As shown in the right figure, the combination of microservices and API gateways can make the service itself more focused on its own domain and isolate service invokers and service providers.
Why Kong?
Spring Cloud players must have heard of Zuul, a routing component that includes frameworks such as Zuul2 and Spring cloud Gateway, and is well known in China. Yes, I call these component Or frameworks, and Kong is a better word for product. Here we can make a simple comparison between Zuul and Kong.
For example, if you choose to use Zuul, when you need to add current-limiting functions to your application, because Zuul only provides basic routing functions, developers need to develop Zuul Filter by themselves. You may not find it troublesome to develop a function, but if you put more demands on Zuul on this basis, it is regrettable that Zuul users need to take on these complexities on their own. For Kong, the current limiting function is a plug-in, which can be used out of the box with simple configuration.
Features
- Cloud-Native: Platform agnostic, Kong can run from bare metal to Kubernetes.
- Dynamic Load Balancing: Load balance traffic across multiple upstream services.
- Hash-based Load Balancing: Load balance with consistent hashing/sticky sessions.
- Circuit-Breaker: Intelligent tracking of unhealthy upstream services.
- Health Checks: Active and passive monitoring of your upstream services.
- Service Discovery: Resolve SRV records in third-party DNS resolvers like Consul.
- Serverless: Invoke and secure AWS Lambda or OpenWhisk functions directly from Kong.
- WebSockets: Communicate to your upstream services via WebSockets.
- OAuth2.0: Easily add OAuth2.0 authentication to your APIs.
- Logging: Log requests and responses to your system over HTTP, TCP, UDP, or to disk.
- Security: ACL, Bot detection, whitelist/blacklist IPs, etc…
- Syslog: Logging to System log.
- SSL: Setup a Specific SSL Certificate for an underlying service or API.
- Monitoring: Live monitoring provides key load and performance server metrics.
- Forward Proxy: Make Kong connect to intermediary transparent HTTP proxies.
- Authentications: HMAC, JWT, Basic, and more.
- Rate-limiting: Block and throttle requests based on many variables.
- Transformations: Add, remove, or manipulate HTTP requests and responses.
- Caching: Cache and serve responses at the proxy layer.
- CLI: Control your Kong cluster from the command line.
- REST API: Kong can be operated with its RESTful API for maximum flexibility.
- Geo-Replicated: Configs are always up-to-date across different regions.
- Failure Detection & Recovery: Kong is unaffected if one of your Cassandra nodes goes down.
- Clustering: All Kong nodes auto-join the cluster keeping their config updated across nodes.
- Scalability: Distributed by nature, Kong scales horizontally by simply adding nodes.
- Performance: Kong handles load with ease by scaling and using NGINX at the core.
- Plugins: Extendable architecture for adding functionality to Kong and APIs.
It is often described as a “drop-in replacement for expensive proprietary API management systems.”
The rough idea behind Kong is to give developers a centralized management layer for microservices and APIs. Kong gives developers a centralized dispatcher they can rely on to talk to the microservices that power their applications and APIs, which can either be public or private.
Kong allows developers to manage authentication, data encryption, logging, rate limiting and other standard features they would expect from a basic API management system. All of this is powered by a straightforward RESTful API, and the platform itself is built on top of the NGINX proxy server and the Apache Cassandra database management system.
The Kong architecture centers around plug-ins. NGINX already offers a plug-in for enabling live monitoring of NGINX Plus instances that run Kong.

